Every time you log in to an app using Google, Facebook, or GitHub, have you ever wondered:
Why don’t I need to enter my password?
The answer is OAuth2 — the open standard that makes secure, delegated access possible.
Today, let’s dive deep into:
- What is OAuth2?
- Why Authorization Code Flow is the gold standard
- Best practices for securing your OAuth2 implementation
1. What is OAuth2? (And why does it matter?)
OAuth2 (Open Authorization 2.0) is a delegated authorization framework that lets applications (clients) access user resources (resource owners) without knowing their passwords.
Instead of handing out the keys to the castle, OAuth2 issues a visitor pass (token) with limited permissions.
Key Components:
- Resource Owner: The user (that’s you!).
- Client: The application requesting access (e.g., a calendar app, CRM system).
- Authorization Server: Authenticates users and issues tokens (e.g., Google Auth, Keycloak).
- Resource Server: Hosts the protected APIs or data.
2. OAuth2 Grant Types: Different Paths for Different Needs
OAuth2 defines several grant types depending on security context:
| Grant Type | Purpose | Ideal Use Case |
|---|---|---|
| Authorization Code (Code Flow) | Highest security | Web apps, mobile (server-side) |
| Implicit | Quick but insecure | Legacy SPAs (not recommended today) |
| Resource Owner Password | Client trusted with user credentials | Legacy systems |
| Client Credentials | Server-to-server communication | Microservices, CRON jobs |
In this post, we’ll focus on Authorization Code Flow — the gold standard for web app security.
3. Authorization Code Flow: The Safest Route for Web Apps
High-Level Flow:
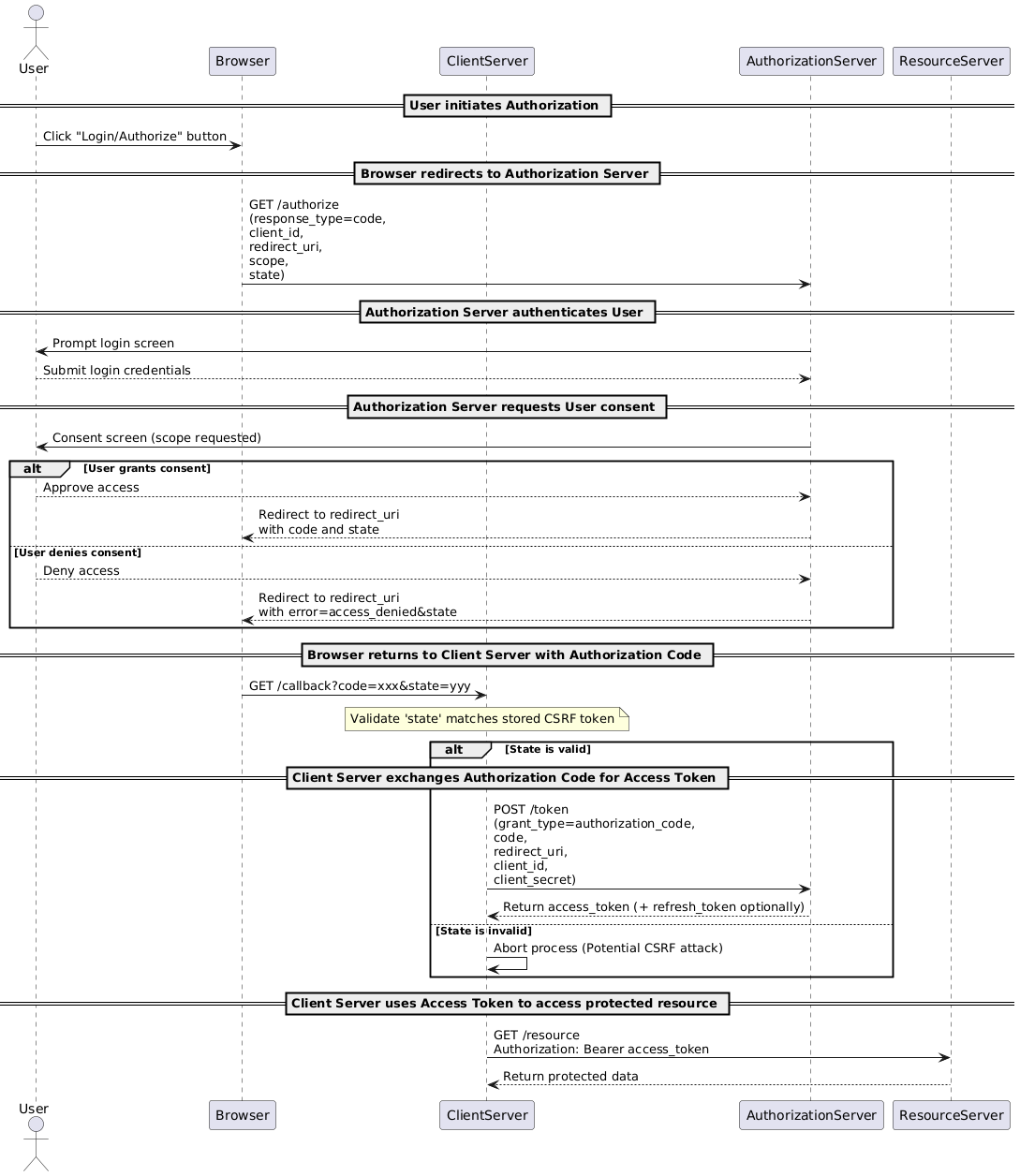
- User clicks “Login”.
- Client redirects the browser to Authorization Server.
- User authenticates and grants permission.
- Authorization Server returns an Authorization Code via redirect.
- Client exchanges the code for an Access Token (and optionally a Refresh Token).
- Client uses the Access Token to call APIs and access resources.
Why is this flow so secure?
- Access tokens are never exposed to the browser directly.
- State parameter prevents CSRF attacks.
- Supports PKCE (Proof Key for Code Exchange) to secure mobile and SPA flows.
4. PKCE: Strengthening the Chain for Mobile and SPAs
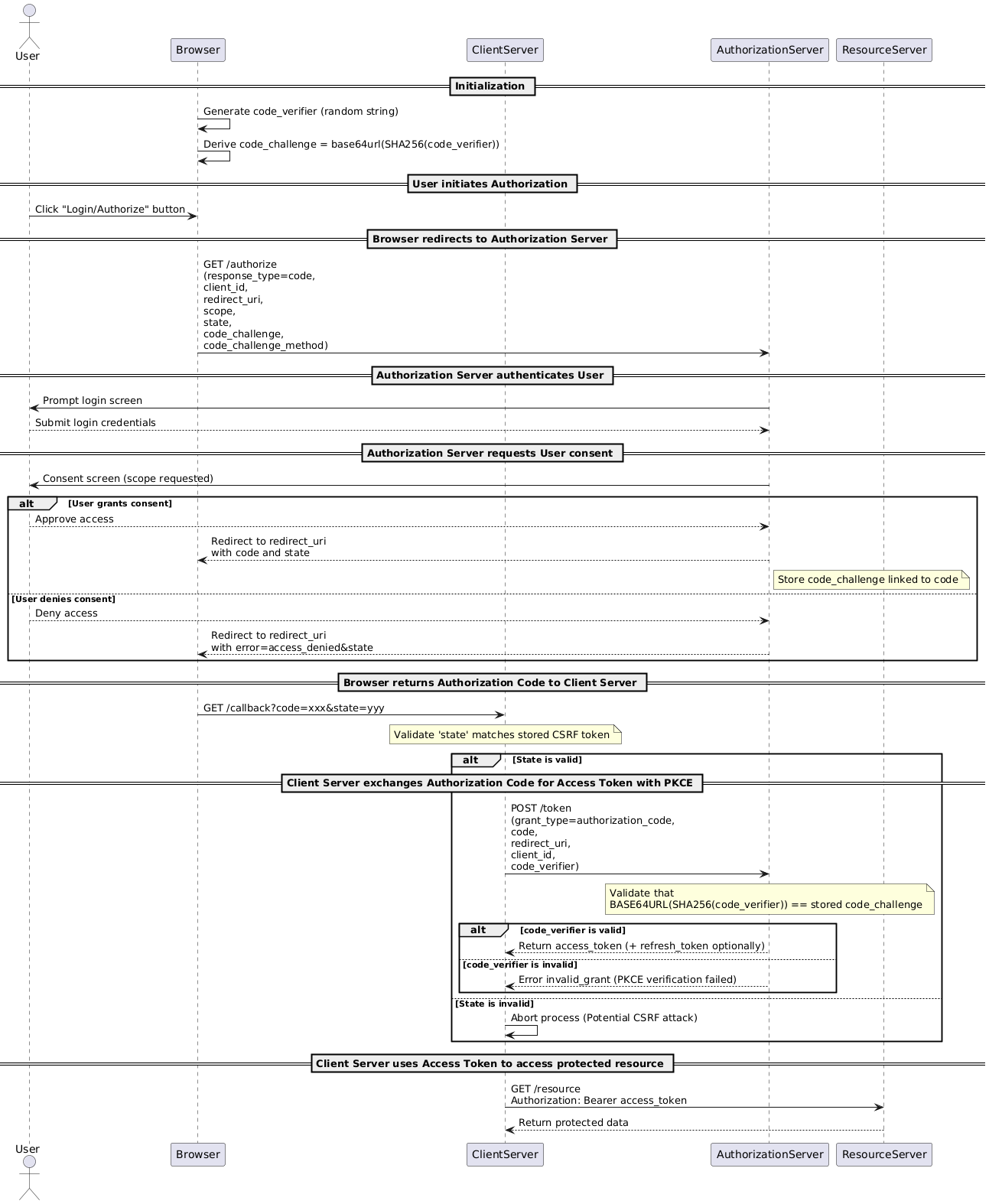
PKCE (Proof Key for Code Exchange) enhances Authorization Code Flow for public clients (like mobile apps where you can’t safely store secrets).
Workflow additions:
- Client generates a code_verifier and derives a code_challenge.
- Authorization Server verifies the code_challenge during the token exchange.
- No client secret needed.
- Prevents interception attacks on Authorization Code.
5. Best Practices: Securing Your OAuth2 Implementation
| Do | Avoid |
|---|---|
| Always use HTTPS | Allowing HTTP at any stage |
Use state and PKCE for CSRF protection |
Omitting state |
| Request minimum required scopes | Asking for overly broad permissions |
| Rotate refresh tokens regularly | Using access tokens without expiration |
Strictly validate redirect_uri |
Using wildcards (*) for redirect URIs |
6. Conclusion: OAuth2 Powers Secure, Scalable Authentication
With OAuth2, you can:
- Increase security by separating authentication from applications.
- Scale easily with microservices and APIs.
- Enhance user experience via Single Sign-On (SSO) and Social Login.
Authorization Code Flow with PKCE is the trusted foundation for modern secure web and mobile applications.
Remember: Security isn’t just encryption — it’s about designing the entire flow correctly!